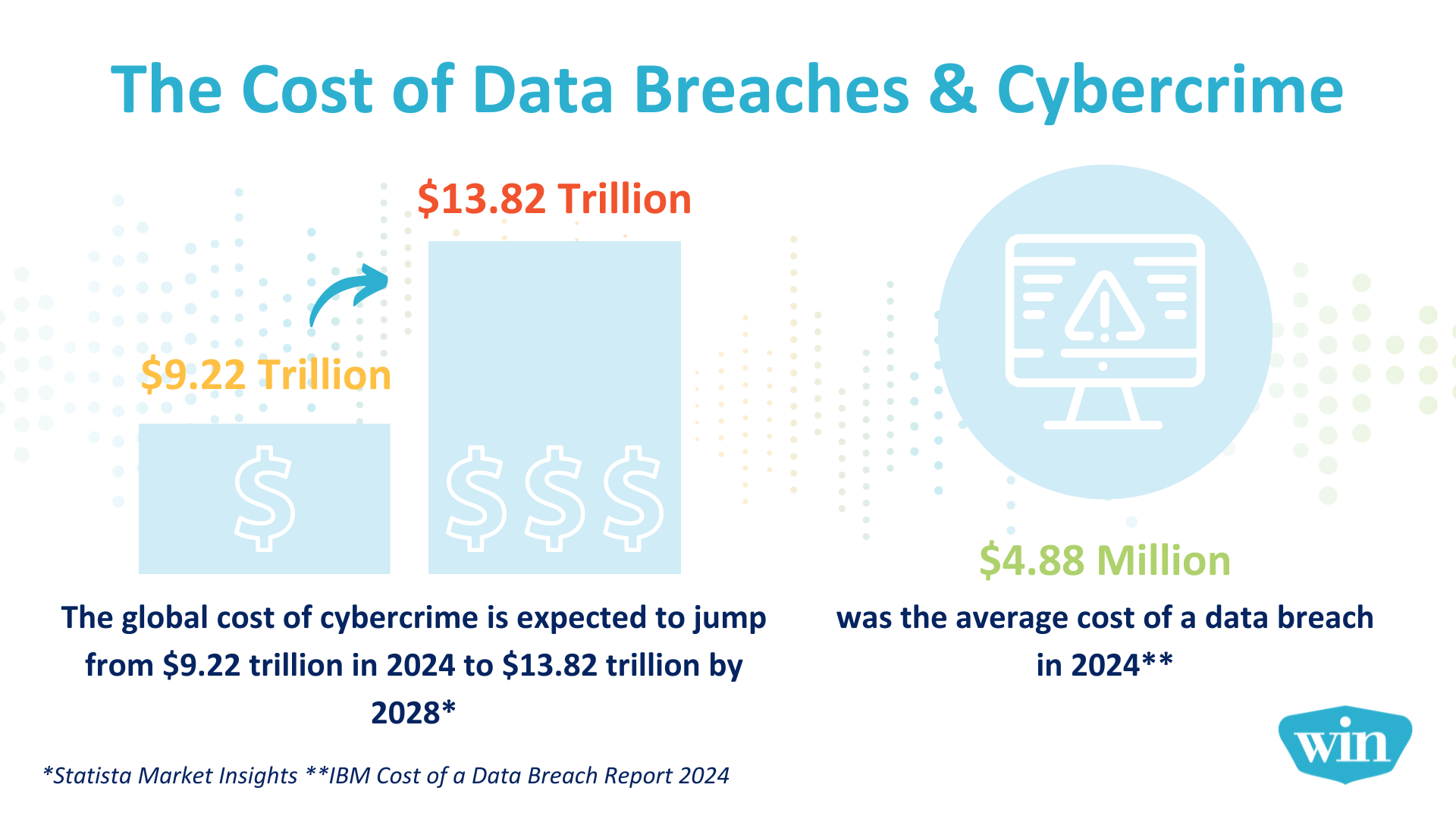
Cybercrime has grown into a multi-trillion-dollar problem affecting businesses of all sizes. Now more than ever, it’s critical to take the right security measures to protect your network and data.
Cybercriminals today will do anything to monetize your network, your data, and your entire business. Hackers will target big and small companies in any business sector in pursuit of money.
The United States Cybersecurity and Infrastructure Security Agency (CISA) routinely warns organizations that they are being targeted by foreign entities and APTs (Advanced Persistent Threats). All businesses need to ensure they are fully protecting their company from the always-evolving, modern-day cyber threat.
Here are nine ways to protect your network, including action items, and their benefits:
1. Utilize Endpoint Privilege Management (EPM), a solution that helps organizations implement Zero Trust endpoint security controls.
Zero Trust is a security framework that assumes that no user or device on a network should be inherently trusted, and that allows users access only to the bare minimum they need to do their job. Here are the five specific components of EPM.
- Whitelisting: This only permits approved files to execute and blocks everything else, allowing IT pros to easily manage which software is allowed to run.
- Application Control: This allows for granular control over what applications are allowed to do. It protects against the weaponization of trusted applications.
- Privileged Access Management: Manage and control privileged access and permissions for users, applications and systems within your IT environment.
- Storage Control: Gives you control over all storage device access.
- Network Access Control: Lockdown endpoints and block inbound and outbound network traffic.
2. Detect and quickly respond to security incidents with Managed Detection and Response (MDR).
MDR is a cybersecurity service that protects your data and assets even if a threat eludes common organizational security controls. This service offers network monitoring, threat detection and response, a security operations center and threat hunting.
3. Stay ahead of cybercriminals with Next-Gen Antivirus.
Cyber attackers are constantly improving their tactics. Your antivirus needs to match them now, and over the next 10 years. A next-generation anti-virus (NGAV/AV) will effectively block hackers in real-time, and quickly analyze and remediate incidents.
4. Build a security culture with cyber user awareness and simulated phishing messages.
Employees are the front-line defense to your company’s security. They can also be the weakest link, so it is critical to inform them of cybersecurity risks. You should provide real-world examples of businesses that have been negatively impacted by cybersecurity issues. This could include productivity decreases, job losses or how employees are placed at risk if their personal and financial information is not protected during a cybersecurity breach. Cybersecurity is everyone’s responsibility and it’s critical that all staff are well-versed in cybersecurity and how cyber hackers attack them. A Cybersecurity User Awareness Program can help deliver measured improvement in your company’s “human firewall.”
5. Implement a Strong Password Management Policy.
Hackers leverage weak or stolen credentials in 61% of security breaches. Passwords are the keys to your systems and data, and hackers are after them. Following good password hygiene is important to ensure someone cannot walk through an open door. It is critical to have a password management system that uses strong, local-only encryption and multi-factor authentication.
6. Leverage SSO for Identity and Access Management.
Tracking which username corresponds with what systems is complicated, but Single Sign-On (SSO) limits the number of usernames and passwords someone needs to remember. SSO also provides a mechanism to audit sign-ins for anomalous and malicious logins and reduces the number of credentials that need to be disabled for offboarding or reset in the event of a security incident.
7. Implement Multi-Factor Authentication (2FA / MFA).
Passwords can be easily stolen, cracked, or guessed by hackers. Adding a second layer of security to your login process can make it much harder for criminals to gain access to sensitive computers and network systems. Using the right software and hardware can enable a user-friendly experience while keeping hackers out of your systems.
8. Optimize firewall security hardening, auditing, and administration.
Firewalls are the perimeter of your network, and if properly configured can prevent outsiders from gaining access to your internal network. Update your firewalls frequently and ensure that your firewall policy rules are not too permissive, allowing hackers to gain a foothold.
9. Improve backups and disaster recovery measures.
In the event of a major incident, backups will be imperative to restore your critical data and systems. System and network backups are a high-priority target for hackers as they want you to pay their ransomware demands. You need to make it as difficult as possible for hackers to delete your backed-up data.
The question is not if, but when, a malicious actor will target your organization. You need to be prepared and make it as difficult as possible for them to achieve their objectives. Network systems need to be configured securely to make sure they’re not a “soft” target. Making it extremely difficult for attackers to compromise, pivot, and escalate privileges in your systems and network will help persuade them to give up and move on to an easier target.
Ready to learn more?
As an IT Services Provider serving customers in Wisconsin, Minnesota, Iowa, Illinois and upper Michigan, we are constantly developing new and innovative ways to protect companies of all sizes and keep them ahead of cyber attackers. If you have questions or want to learn more, talk to a WIN Specialist.
