Businesses today, especially Small-Medium Businesses (SMBs), are facing more cybersecurity challenges than ever. This includes ransomware, phishing, supply chain, cloud and IoT threats.
Percentage of companies compromised by at least one successful cyber attack
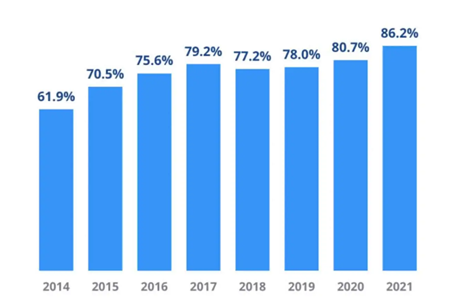
Source: CyberEdge Group 2021 Cyber Security Threat Report
- Almost half of all cyber breaches impact businesses with fewer than 1,000 employees
- 82% of recent ransomware attacks were against companies with less than 1,000 employees
Control the risks you can and be prepared for the ones you can’t.
There are many internal cyber security risks, such as human factors, IT infrastructure and cash flow. A good cyber security partner can put controls around those risks.
You cannot manage certain external risks such as market changes, natural disasters and your competition. Cybersecurity experts can put safety nets in place to better manage your risks and protect you from the effects of cyber attacks.
Cybersecurity framework: What is it and how and it reduces risk?
Cybersecurity frameworks are an industry best practice to better manage risk. They can help you align your risk management strategy and avoid cyber attacks. These frameworks also allow you to align cybersecurity with your business needs and measure what is being accomplished in a more quantitative way. They validate what is being done well and let you change your focus to areas that need improvement. Frameworks can help you identify and set priorities as well as tell you where you land on the maturity scale.
What are some common cybersecurity frameworks?
Four of the most common cybersecurity frameworks are:
1) National Institute of Standards and Technology Cyber Security Framework (NIST CSF)
2) Center for Internet Security (CIS) Top 18
3) Open Worldwide SecurityProject (OWASP) Top 18
4) Information Organization for Standardization/International Electrotechnical Commission (ISO/IEC) 27001
NIST Cybersecurity Frameworks guidelines?
NIST Cybersecurity Framework is one of the most popular set of guidelines for mitigating organizational cybersecurity risks, so we’ll go into detail about it here. It’s published by the US National Institute of Standards and Technology and based on existing standards, guidelines, and practices.
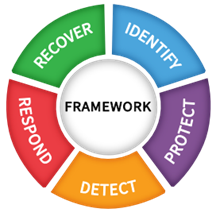
1. Identify: What should we protect?
Make a list of all equipment, software, and data you use, including laptops, smartphones, tablets, and point-of-sale devices.
Create and share a company cybersecurity policy that covers roles and responsibilities for employees, vendors, and anyone else with access to sensitive data. Finally, you should lay out the steps required to protect against an attack and limit the damage if one occurs.
2. Protect – what safeguards are in place?
First, you need to control who logs on to your network and uses your computers and other devices. Use security software to protect data, encrypt sensitive data, at rest and in transit. You should also conduct regular backups of data, update security software regularly, and automate those updates if possible. Formal policies need to be in place for safely disposing of electronic files and old devices. Finally, you should train everyone who uses your computers, devices, and network about cybersecurity. You can help employees understand their personal risk in addition to their crucial role in the workplace.
3. Detect – how do we know an event occurred?
Investigate any unusual activities on your network or by your staff and check your network for unauthorized users or connections. Consider implementing an Endpoint Detection and Response (EDR) tool to assist with identifying suspicious behavior and potential breaches.
4. Respond – can we stop it, and can we analyze what happened?
You need to have a detailed plan for investigating and containing any cyber attack for two reasons. First, to notify customers, employees, and others whose data may be at risk and second, to keep business operations up and running. You need to report any attack to law enforcement and other authorities, updating your cybersecurity policy and plan with lessons learned and preparing for inadvertent events (like weather emergencies) that may put data at risk.
5. Recover – how do we put the pieces back together?
After an attack, you need to repair and restore the equipment and parts of your network that were affected as well as keep employees and customers informed of your response and recovery activities.
There are some limitations to cybersecurity frameworks
Even with all its benefits, a cybersecurity framework will not eliminate or solve all of your cybersecurity risks. It’s a helpful tool and a way to track your progress over time but even full compliance does not equal full security. You still need to rely on control, implementation, configuration and maintenance.
Top priorities within frameworks
There are eight key priorities within cybersecurity frameworks:
1) Data recovery
2) Security awareness training
3) Malware defense
4) Mult-factor Authentication (MFA)
5) Endpoint Detetion and Response (EDR)
6) Backups and backup recovery
7) Access management
8) Vulnerability management
How can you get started with cybersecurity frameworks?
First you’ll want to make sure you partner with a cybersecurity expert who has frameworks experience. Next, determine if any external entities require following a specific framework. Once the plan is in place, you need to annually assess your progress against the framework.
Ready to learn more?
If you have questions or want to lean more, talk to a WIN Specialist or email [email protected].
